
The U.S. Federal Bureau of Investigation (FBI) is warning investors that cybercriminals are increasingly exploiting security vulnerabilities in Decentralized Finance (DeFi) platforms to steal cryptocurrency.
“The FBI has observed cyber criminals exploiting vulnerabilities in the smart contracts governing DeFi platforms to steal investors’ cryptocurrency,” the federal law enforcement agency said.
“The FBI encourages investors who suspect cyber criminals have stolen their DeFi investments to contact the FBI via the Internet Crime Complaint Center or their local FBI field office.”
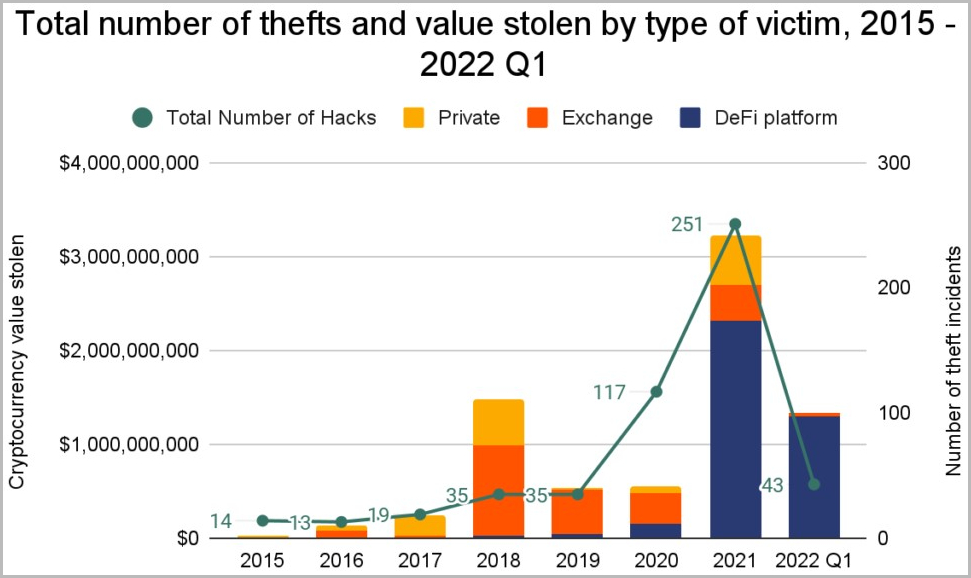
The public service announcement, published on the FBI’s Internet Crime Complaint Center (IC3) today, adds that out of roughly $1.3 billion in cryptocurrency stolen between January and March 2022, snatched almost 97 percent of it from DeFi platforms.
Per FBI’s calculations, this amounts to a significant increase from 72 percent in 2021 and approximately 30 percent in 2020, respectively.
Attackers have used various methods to hack and steal cryptocurrency from DeFi platforms, including initiating flash loans that trigger exploits in the platforms’ smart contracts and exploiting signature verification flaws in their token bridge to withdraw all investments.
The agency has also observed cybercriminals manipulating crypto price pairs by exploiting chains of vulnerabilities, including the DeFi platforms’ use of a single price oracle and then conducting leveraged trades to bypass slippage checks.
The FBI recommends investors take precautions before making an investment decision, such as to:
- Research DeFi platforms, protocols, and smart contracts before investing and be aware of the specific risks involved in DeFi investments.
- Ensure the DeFi investment platform has conducted one or more code audits performed by independent auditors. A code audit typically involves a thorough review and analysis of the platform’s underlying code to identify vulnerabilities or weaknesses in the code that could negatively impact the platform’s performance.
- Be alert to DeFi investment pools with extremely limited timeframes to join and rapid deployment of smart contracts, especially without the recommended code audit.
- Be aware of the potential risk posed by crowdsourced solutions to vulnerability identification and patching. Open source code repositories allow unfettered access to all individuals, including those with nefarious intentions.
DeFi platforms under heavy targeting
FBI’s warning follows a Chainalysis report from April that highlighted how, according to Q1 2022 data, DeFi cryptocurrency platforms are now more targeted than ever.
In most incidents, the attackers rely on exploiting security vulnerabilities in their code or a security breach on the platform, allowing them to siphon cryptocurrency to addresses under their control.
According to Chainalysis, threat actors behind such attacks have laundered most of the stolen assets in 2022 using risky laundering services such as illegal exchanges and coin tumblers on the dark web.
While in 2021, around 25% of all cryptocurrency stolen from DeFi platforms was later recovered and returned to the victims, this year no DeFi-stolen funds have been returned, showing that attackers are less interested in securing their stolen assets.
In April, the FBI linked the hack of Axie Infinity’s Ronin network bridge, now the largest crypto hack ever, to the Lazarus and BlueNorOff (aka APT38) North Korean threat groups.
The previous most significant theft of cryptocurrency was the $611 million hack of the decentralized cross-chain protocol and network Poly Network in August 2021.
“Cyber criminals seek to take advantage of investors’ increased interest in cryptocurrencies, as well as the complexity of cross-chain functionality and open source nature of DeFi platforms,” further warned the FBI today.
“Investors should make their own investment decisions based on their financial objectives and financial resources and, if in any doubt, should seek advice from a licensed financial adviser.”
This news is republished from another source. You can check the original article here



